Qop In Sip
With transport layer security tls mutual authentication of proxies or a proxy and ua is accomplished using certificates. This document shows the creation of a smm rule table that selects only certain sip messages for modification.
 Queen Of Pain Tsunami S Dota Hero Tips And Counters
Queen Of Pain Tsunami S Dota Hero Tips And Counters
Sip implementors nonce and response values in re register.

Qop in sip. Authentication is enabled at the outbound server and it challenges alices client. Sip authentication challenge when the oracle enterprise communications broker receives a response from the hss including the hash value for the user it sends a sip authentication challenge to the endpoint if the endpoint did not provide any authentication headers in its initial contact the with oracle enterprise communications broker. The epid parameter on the from.
Sip authentication model based on the http digest authentication described in the rfc 2617. The problem is that if qop parameter does not arrive in the challenge 401407 and the algo for the session is md5 sess then hash key a1 is built with cnonce value at the client but cnonce value is not sent to the server in the subsquent requests. If quality of protection qop is not specified by the server the client will operate in a security reduced legacy rfc 2069 mode.
The server indicates support for tls dsk kerberos and ntlm in the challenge and returns the realm and targetname values that it created during initialization the version of the authentication protocol that it implements and the date header field. This document details how to configure the sbc to remove brackets from a the uri parameter in a proxy authentication header. Hi all i try to register some basic sip phones to cisco isr 4331.
Shouldit be same as previous register event for auth andauth int qop options. My sip phone has username 60401 password60401 and the voip routergw sends a 401 unauthorized. For example a mitm attacker could tell clients to use basic access authentication or legacy rfc2069 digest access authentication mode.
Authentication is enabled at the server which then challenges alices client. The server uses this value in subsequent messages to determine the sa with which to sign the message. Digest access authentication is vulnerable to a man in the middle mitm attack.
Sip user authentication there are two forms of authentication in sip authentication of a user agent ua by a proxy redirect or registration server and authentication of one ua by another. This post is intended to be a neutral in its analysis of the vendors sip registration process and the various vendors registration responses as analyzed in wire shark using the conterpath free x lite soft phone. But i dont see why because register looks ok can someone pls help and have a look.
Header uniquely identifies this particular endpoint for the user.
 Ms Sip Best Effort Notify Example Microsoft Docs
Ms Sip Best Effort Notify Example Microsoft Docs
Yate Client Not Available Onsip Support
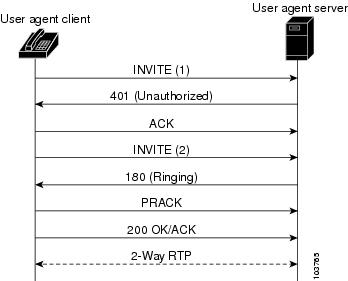 Sip Configuration Guide Cisco Ios Release 15m T Configuring Sip
Sip Configuration Guide Cisco Ios Release 15m T Configuring Sip
 The Sip Digest Authentication A Representation Of This
The Sip Digest Authentication A Representation Of This
 Understanding Sip Authentication Tao Zen And Tomorrow
Understanding Sip Authentication Tao Zen And Tomorrow
 Removing Brackets From A Parameter Using Sip Message Manipulation
Removing Brackets From A Parameter Using Sip Message Manipulation
Https Conference Hitb Org Hitbsecconf2019ams Materials Haxpo 20d2 20 20attacking 20encrypted 20voip 20protocols 20 20ivica 20stipovic Pdf

 Packetcable 2 0 Hss Technical Report Pkt Tr Hss V Released
Packetcable 2 0 Hss Technical Report Pkt Tr Hss V Released
 Jain Sip Authentication Stack Overflow
Jain Sip Authentication Stack Overflow
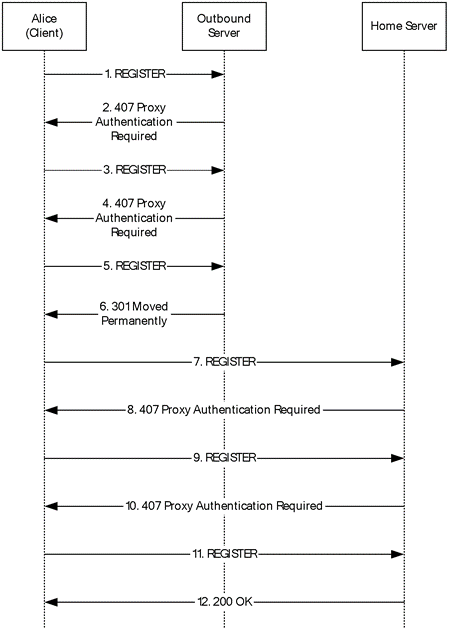 Ms Sip Registration With Ntlm Microsoft Docs
Ms Sip Registration With Ntlm Microsoft Docs